
week
A software company that serves more than 10,000 courtrooms worldwide hosted an application update containing a hidden backdoor that maintains constant communication with a malicious website, researchers reported Thursday, in the latest episode of a supply chain attack.
The software, known as JAVS Viewer 8, is an integral part of JAVS Suite 8, an application suite used by courtrooms to record, play back and manage audio and video recordings of proceedings. Its manufacturer, Justice AV Solutions, based in Louisville, Kentucky, says its products are used in more than 10,000 courtrooms in the United States and 11 other countries. The company has been operating for 35 years.
High-risk users of JAVS Viewer
Researchers at security firm Rapid7 reported that the version of JAVS Viewer 8 available for download on javs.com contained a backdoor that gave an unknown threat actor permanent access to infected devices. The malicious download, embedded in an executable file that installs JAVS Viewer version 8.3.7, was available as late as April 1, when the announcement was made on X (formerly Twitter). It is not clear when the hijacked version was removed from the company’s download page. JAVS representatives did not immediately respond to emailed questions.
Users who installed version 8.3.7 of the JAVS Viewer executable are at high risk and should act immediately, said Rapid7 researchers Ipek Solak, Thomas Elkins, Evan McCann, Matthew Smith, Jake McMahon, Tyler McGraw, Ryan Emmons, Stephen Fewer and written by John Fenninger. This version contains a backdoor installer that allows attackers to take full control of affected systems.
The installation file was titled JAVS Viewer Setup 8.3.7.250-1.exe. When executed, it copies the binary file fffmpeg.exe to the file path C:\Program Files (x86)\JAVS\Viewer 8\. To bypass the security warnings, the installer was digitally signed, but with the signature issued to an entity called Vanguard Tech Limited, not Justice AV Solutions Inc., the signing entity used to authenticate legitimate JAVS software.
fffmpeg.exe, in turn, used Windows Sockets and WinHTTP to establish communication with the command and control server. After successful login, fffmpeg.exe submitted server passwords collected from the browser and information about the compromised host, including host name, operating system details, processor architecture, program working directory, and user name.
The researchers said fffmpeg.exe I also downloaded the file chrome_installer.exe from IP address 45.120.177.178. chrome_installer.exe then executed the binary and several Python scripts responsible for stealing passwords saved in browsers. fffmpeg.exe is related to a well-known malware family called GateDoor/Rustdoor. The EXE file has already been reported by 30 endpoint protection mechanisms.
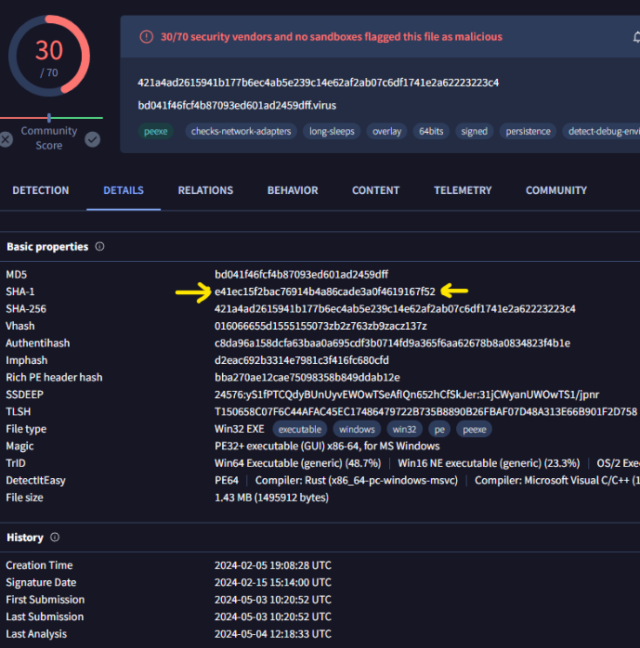
Increase / A screenshot from VirusTotal showing the detections of 30 endpoint protection mechanisms.
Quick7
The number of detections has risen to 38 at the time of this post.
The researchers cautioned that the process of disinfecting infected devices will require precautions. They wrote:
To resolve this issue, affected users should:
- Reimage all endpoints that have JAVS Viewer 8.3.7 installed. Simply uninstalling the software is not enough, as attackers may have planted additional backdoors or malware. Reimaging gives a clean slate.
- Reset the credentials of all accounts associated with the affected endpoints. This includes local accounts on the endpoint itself as well as any remote accounts that can be accessed during the installation period of JAVS Viewer 8.3.7. Attackers may have stolen credentials from compromised systems.
- Reset the credentials used in the web browsers on the affected endpoints. Browser sessions may have been hijacked to steal cookies, stored passwords, or other sensitive data.
- Install the latest version of JAVS Viewer (8.3.8 or later) after reimaging the affected systems. The new version does not contain the backdoor present in 8.3.7.
It is imperative to fully resurface affected endpoints and revoke associated credentials to ensure that attackers have not persisted through backdoors or stolen credentials. All organizations using JAVS Viewer 8.3.7 should take these steps immediately to fix the compromise.
The Rapid7 post included a statement from JAVS confirming that the JAVS Viewer version 8.3.7 installer is malicious.
We have pulled all versions of Viewer 8.3.7 from the JAVS website, reset all passwords and conducted a full internal audit of all JAVS systems, the statement said. We have confirmed that all files currently available on the JAVS.com website are genuine and free of malware. We have further confirmed that JAVS source code, certificates, systems or other software versions were not compromised in this incident.
The statement does not explain how the installer became available for download on the website. He also did not say whether the company hired an outside firm to investigate.
This incident is the latest example of a supply chain attack, a technique that tampers with a legitimate service or software with the goal of infecting all downstream users. This type of attack is usually performed by first hacking the service or software provider. There’s no foolproof way to avoid becoming a victim of a supply chain attack, but one potentially useful measure is to scan the file with VirusTotal before running. This tip would serve JAVS users well.
