Almost half of the breaches in EMEA were initiated internally. A finding that would show a high frequency of privilege abuse and other human errors.
The majority of breaches worldwide (68%), whether involving third parties or not, involve non-malicious human actions, which refers to someone making a mistake or falling victim to a social engineering attack.
This is according to Verizon’s 17th Annual Data Breach Investigations Report, which analyzed 8,302 security incidents in Europe, the Middle East and Africa (EMEA), including 6,005 (more than 72%) confirmed breaches.
The percentage of 68% is close to last year’s. On the other hand, on the positive side, reporting practices are improving: 20% of users identified and reported phishing in simulations, and 11% who clicked on an email also reported it.
Zero-day vulnerabilities
Despite this small point of optimism, it is clear that reading this report does not give peace of mind: vulnerability exploitation increased by 180% compared to 2023 and on average it took about 55 days for organizations to fix 55% of their critical vulnerabilities. Meanwhile, the average time to detect massive KEV CISA attacks on the Internet is five days.
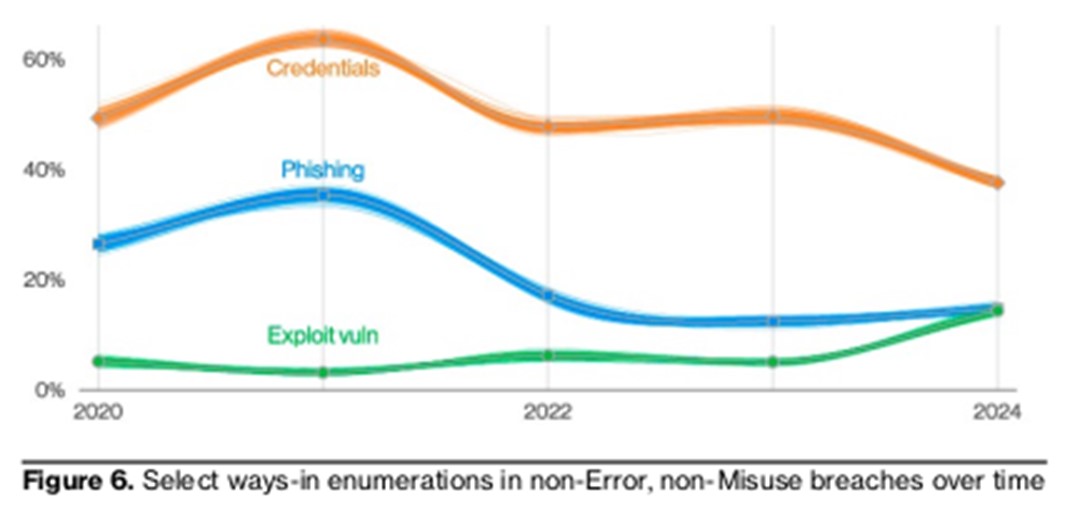
Like other studies, this one finds that it is a factor human remains a gateway for cybercriminals. This persistence shows that organizations in EMEA must continue to combat this trend by prioritizing training and awareness of cybersecurity best practices.
Another concern, vulnerabilities ” zero day » remain a constant threat to businesses Globally, exploitation of vulnerabilities as an initial entry point has increased since last year, accounting for 14% of all breaches.
Supply chain
This increase is primarily driven by the scale and increasing frequency of zero-day exploitation by ransomware actors. Especially the MOVEit bug, a widespread exploitation of the “zero-day” vulnerability.
“The exploitation of zero-day vulnerabilities by ransomware actors remains a constant threat to businesses, due to the interconnectedness of supply chains” said Alistair Neil.
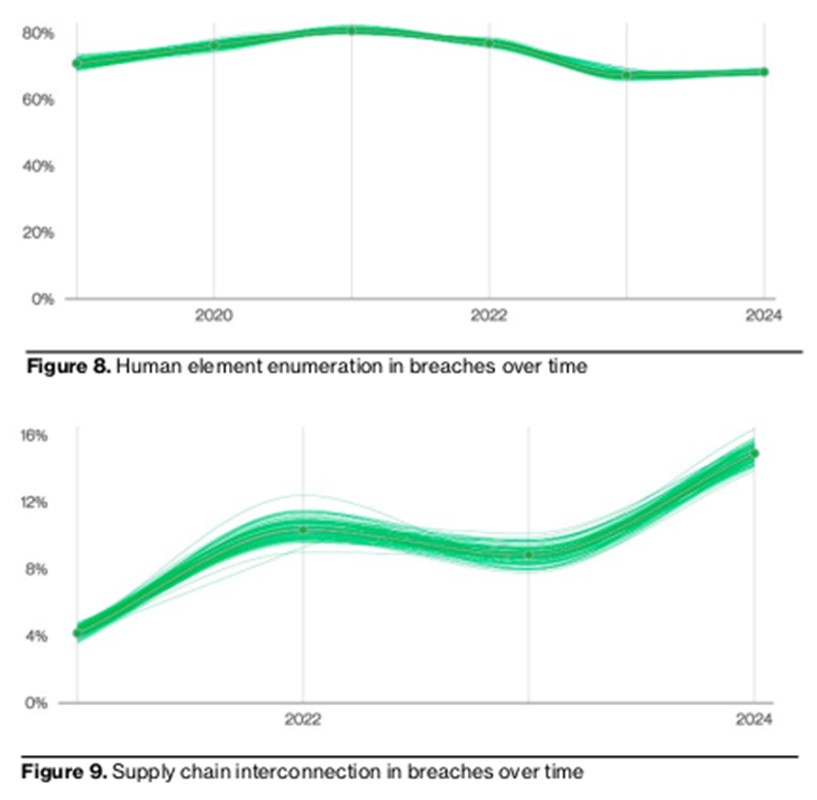
“Last year, 15% of breaches involved a third party, including data providers, third-party software vulnerabilities and other direct or indirect supply chain issues”specifies this senior director of security at Verizon Business.
Analysis of the Cybersecurity Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) catalog found that organizations need an average of 55 days to fix 50% of critical vulnerabilities after patches become available.
Finally, a third of all breaches involved some type of extortion technique, including ransomware. Over the past two years, about a quarter (between 24% and 25%) of financially motivated incidents involved an excuse.

